Online Cheating Site AshleyMadison Hacked
Large caches of data stolen from online cheating site AshleyMadison.com have been posted online by an individual or group that claims to have completely compromised the company’s user databases, financial records and other proprietary information. The still-unfolding leak could be quite damaging to some 37 million users of the hookup service, whose slogan is “Life is short. Have an affair.”
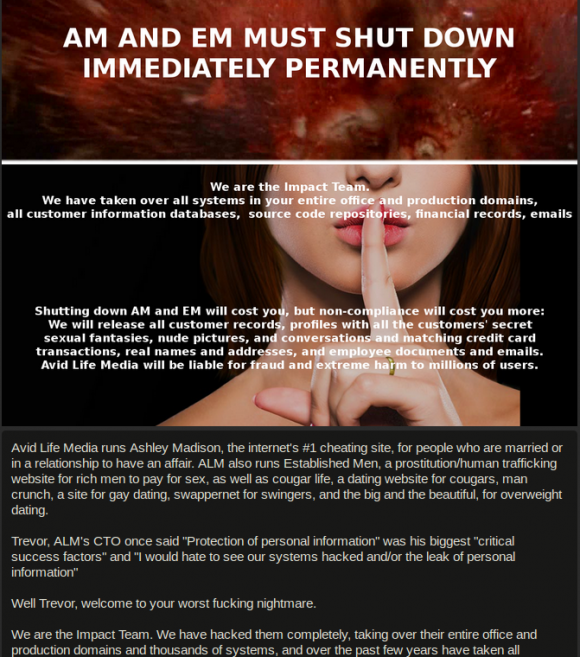
The data released by the hacker or hackers — which self-identify as The Impact Team — includes sensitive internal data stolen from Avid Life Media (ALM), the Toronto-based firm that owns AshleyMadison as well as related hookup sites Cougar Life and Established Men.
Reached by KrebsOnSecurity late Sunday evening, ALM Chief Executive Noel Biderman confirmed the hack, and said the company was “working diligently and feverishly” to take down ALM’s intellectual property. Indeed, in the short span of 30 minutes between that brief interview and the publication of this story, several of the Impact Team’s Web links were no longer responding.
“We’re not denying this happened,” Biderman said. “Like us or not, this is still a criminal act.”
Besides snippets of account data apparently sampled at random from among some 40 million users across ALM’s trio of properties, the hackers leaked maps of internal company servers, employee network account information, company bank account data and salary information.
The compromise comes less than two months after intruders stole and leaked online user data on millions of accounts from hookup site AdultFriendFinder.
In a long manifesto posted alongside the stolen ALM data, The Impact Team said it decided to publish the information in response to alleged lies ALM told its customers about a service that allows members to completely erase their profile information for a $19 fee.
According to the hackers, although the “full delete” feature that Ashley Madison advertises promises “removal of site usage history and personally identifiable information from the site,” users’ purchase details — including real name and address — aren’t actually scrubbed.
“Full Delete netted ALM $1.7mm in revenue in 2014. It’s also a complete lie,” the hacking group wrote. “Users almost always pay with credit card; their purchase details are not removed as promised, and include real name and address, which is of course the most important information the users want removed.”
Their demands continue:
“Avid Life Media has been instructed to take Ashley Madison and Established Men offline permanently in all forms, or we will release all customer records, including profiles with all the customers’ secret sexual fantasies and matching credit card transactions, real names and addresses, and employee documents and emails. The other websites may stay online.”
It’s unclear how much of the AshleyMadison user account data has been posted online. For now, it appears the hackers have published a relatively small percentage of AshleyMadison user account data and are planning to publish more for each day the company stays online.
“Too bad for those men, they’re cheating dirtbags and deserve no such discretion,” the hackers continued. “Too bad for ALM, you promised secrecy but didn’t deliver. We’ve got the complete set of profiles in our DB dumps, and we’ll release them soon if Ashley Madison stays online. And with over 37 million members, mostly from the US and Canada, a significant percentage of the population is about to have a very bad day, including many rich and powerful people.”
ALM CEO Biderman declined to discuss specifics of the company’s investigation, which he characterized as ongoing and fast-moving. But he did suggest that the incident may have been the work of someone who at least at one time had legitimate, inside access to the company’s networks — perhaps a former employee or contractor.
“We’re on the doorstep of [confirming] who we believe is the culprit, and unfortunately that may have triggered this mass publication,” Biderman said. “I’ve got their profile right in front of me, all their work credentials. It was definitely a person here that was not an employee but certainly had touched our technical services.”
As if to support this theory, the message left behind by the attackers gives something of a shout out to ALM’s director of security.
“Our one apology is to Mark Steele (Director of Security),” the manifesto reads. “You did everything you could, but nothing you could have done could have stopped this.”
Several of the leaked internal documents indicate ALM was hyper aware of the risks of a data breach. In a Microsoft Excel document that apparently served as a questionnaire for employees about challenges and risks facing the company, employees were asked “In what area would you hate to see something go wrong?”
Trevor Stokes, ALM’s chief technology officer, put his worst fears on the table: “Security,” he wrote. “I would hate to see our systems hacked and/or the leak of personal information.”
In the wake of the AdultFriendFinder breach, many wondered whether AshleyMadison would be next. As the Wall Street Journal noted in a May 2015 brief titled “Risky Business for AshleyMadison.com,” the company had voiced plans for an initial public offering in London later this year with the hope of raising as much as $200 million.
“Given the breach at AdultFriendFinder, investors will have to think of hack attacks as a risk factor,” the WSJ wrote. “And given its business’s reliance on confidentiality, prospective AshleyMadison investors should hope it has sufficiently, er, girded its loins.”
Update, 8:58 a.m. ET: ALM has released the following statement about this attack:
“We were recently made aware of an attempt by an unauthorized party to gain access to our systems. We immediately launched a thorough investigation utilizing leading forensics experts and other security professionals to determine the origin, nature, and scope of this incident.”“We apologize for this unprovoked and criminal intrusion into our customers’ information. The current business world has proven to be one in which no company’s online assets are safe from cyber-vandalism, with Avid Life Media being only the latest among many companies to have been attacked, despite investing in the latest privacy and security technologies.”“We have always had the confidentiality of our customers’ information foremost in our minds, and have had stringent security measures in place, including working with leading IT vendors from around the world. As other companies have experienced, these security measures have unfortunately not prevented this attack to our system.”“At this time, we have been able to secure our sites, and close the unauthorized access points. We are working with law enforcement agencies, which are investigating this criminal act. Any and all parties responsible for this act of cyber–terrorism will be held responsible.”“Avid Life Media has the utmost confidence in its business, and with the support of leading experts in IT security, including Joel Eriksson, CTO, Cycura, we will continue to be a leader in the services we provide. “I have worked with leading companies around the world to secure their businesses. I have no doubt, based on the work I and my company are doing, Avid Life Media will continue to be a strong, secure business,” Eriksson said.”

No comments:
Post a Comment